AgileAssets supports using OpenID protocol to conduct Single Sign-On (SSO). This topic explains how to setup OpenID with TrimbleID as Identity Provider (IdP). For other IdPs, the process will be similar.
Note:
- Setting up OpenID requires System Admin access on application server, and write access to Tomcat folder.
- The following guide uses https://quappv21.agileassets.com/ams-web as an example AMS application. Update this URL accordingly when configuring a real-world instance.
Click to jump to a section:
IdP Configuration
Ask client's IdP Admin to register the AMS application in IdP, and provide with AgileAssets System Admin these OpenID parameters:
Field | Comments | Example |
|---|---|---|
| Base URL | This is the base URL of the Identity Provider | https://stage.id.trimblecloud.com |
| Application Name/Scope | This is the AMS application name (or scope) assigned in the Idp | AgileAssets AMS |
Client ID | This is the AMS application ID assigned by the Idp | abc-def-ghi-jkl-mno |
Client Secrete | This is the client secrete assigned by the IDP | [Redacted] |
OAuth Authorization Endpoint | OpenID Authorization End point | /oauth/authorize |
| OAuth Token Endpoint | OpenID Token End point | /oauth/token |
| OAuth User Info Endpoint | OpenID User information End point | /oauth/userinfo |
Idp configuration will also need a Redirect URL (or Call Back URL) from AMS. The URL is the application URL appended with /sso at the end. In this example, it will be https://quappv21.agileassets.com/ams-web/sso
AMS Configuration
Encrypt Client Secret
Use the ams-encrypter.jar included the deployment package to encrypt the Client Secret. For example, run this command from the package:
java -jar target\ams-encrypter-7.7.5.0-SNAPSHOT.jar
Follow the prompt and enter the original Client Secret, and obtain the Encrypted Client Secret. It should be a string that starts with @aaEncrypted@, for example, @aaEncrypted@ABCEDFG
Web.xml
Make the following changes in AMS's web.xml file under Tomcat application folder. Note this section in web.xml file is by default commented out. Make sure to un-comment this section.
<servlet>
<servlet-name>SsoServlet</servlet-name>
<servlet-class>com.agileassetsinc.core.servlet.SsoServlet</servlet-class>
<load-on-startup>1</load-on-startup>
</servlet>
<servlet-mapping>
<servlet-name>SsoServlet</servlet-name>
<url-pattern>/sso</url-pattern>
</servlet-mapping>
<filter>
<filter-name>OpenIdSSOFilter</filter-name>
<filter-class>com.agileassetsinc.core.OpenidSsoFilter</filter-class>
<init-param>
<param-name>openIdBaseUrl</param-name>
<param-value>Base URL (eg: https://stage.id.trimblecloud.com)</param-value>
</init-param>
<init-param>
<param-name>openIdScope</param-name>
<param-value>Application Name (eg: AgileAssets AMS)</param-value>
</init-param>
<init-param>
<param-name>openIdClientId</param-name>
<param-value>Client ID (eg: abc-def-ghi-jkl-mno)</param-value>
</init-param>
<init-param>
<param-name>openIdClientSecretEncrypted</param-name>
<param-value>Encrypted Client Secret (eg: @aaEncrypted@ABCDEFG)</param-value>
</init-param>
<init-param>
<param-name>openIdOauthAuthorizationEndpoint</param-name>
<param-value>OpenID Authorization End point (eg: /oauth/authorize)</param-value>
</init-param>
<init-param>
<param-name>openIdOauthTokenEndpoint</param-name>
<param-value>OpenID Token End point (eg: /oauth/token)</param-value>
</init-param>
<init-param>
<param-name>openIdOauthUserinfoEndpoint</param-name>
<param-value>OpenID User information End point (eg: /oauth/userinfo)</param-value>
</init-param>
</filter>
<filter-mapping>
<filter-name>OpenIdSSOFilter</filter-name>
<url-pattern>/sso</url-pattern>
</filter-mapping>
User Configuration
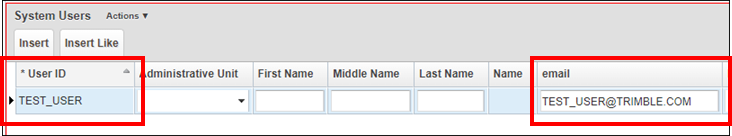
On the System > Security > User Level > User Names and Access window, add each user's Email in OpenID to the Email field at this window.
SSO Login URL
The SSO Login URL is the application URL appended with /sso. For example, https://quappv21.agileassets.com/ams-web/sso, or http://trimbleid.agileassets.com/ams-web/sso
Known Issue
Currently, AgileAssets cannot conduct SSO with Azure using OpenID. For SSO with Azure, please use SAML protocol. See Setup SAML for Single Sign-On for details.